Battery and Energy Technologies |
 |
|
Enigma's Secrets
How it Worked and How the Code was Broken
By way of introduction, see the Historical Background to Enigma and the Key Players Involved. The Working Principle - The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine. What made the machine special however was that for each keystroke there were 158,962,555,217,826,360,000 possible ways of generating the substitute letter or ciphertext from the 26 in the alphabet in what appeared to be a random choice, though selecting the same letter was not allowed. In fact it was not a random choice but depended on the order in which its rotors were placed in the machine, the starting position of each rotor, the internal wiring within each rotor and the connections on a plugboard. The rotors provided 17,576 possible letter substitutions for each keystroke and because at least one of the rotors moved by one position with each keystroke, every keystroke would generate a different ciphertext, even for the same plaintext letter. Traditional encryption schemes were mostly based on simple letter transposition or substitution and decryption often depended on identifying the relative frequency of occurrence of different letters in the ciphertext. Relatively few permutations were possible and once a ciphertext substitution had been identified it could usually be applied for each instance of the corresponding plaintext symbol in the message. By contrast, the probability of a particular Enigma ciphertext symbol representing any plaintext input symbol depends on 159 X 1018 possible permutations and is different for every keystroke and furthermore, the frequency of occurrence of all letters in the Enigma ciphertext is exactly the same. There is no weighting factor associated with different plaintext letters. Checking all 159 X 1018 possible letter substitutions, even by machine, was clearly impractical and that's just for one message. The security and intelligence services however had to decrypt several thousand messages every day. The machine settings were also changed daily so that any minor decryption discoveries would have a very limited useful lifetime. The Enigma Code was therefore thought to be unbreakable.
The Construction - Early versions of the machine had three rotors (wheels) mounted freely on a single spindle, which together were called the "scrambler", and a "QWERTZUIO" keyboard which was standard in Germany but it was upper case only and had no number keys or punctuation keys. Numbers had to be written in text form. Enigma also had a "lampboard", similar to the keyboard, which indicated the ciphertext corresponding to the input key which had been pressed. A battery provided the electrical current to indicate the ciphertext generated by the machine. Later machines also had a plugboard. (See image opposite and also diagram below) The Rotors - Because positions of the scrambler's three rotors on the spindle were interchangeable, they could be installed in any one of six rotor orders, increasing the number of possible ways of encrypting the text. Each of the three rotors had 26 possible angular positions to match the 26 letters of the alphabet and 26 pairs of fixed input and output terminals connecting opposite faces of the rotor wheels which passed the signal from one rotor to the next. The input terminals were spring loaded and connected by internal wires inside the rotor core to flat circular output terminals on the opposite face of the rotor so that each input letter was connected to a different letter on the opposite side of the rotor, thus substituting a different letter as the signal passed through each rotor.
This had two advantages: Reciprocity meant that, with the same settings, any Enigma machine could be used to either encipher or decipher the messages so that typing in the plaintext message would produce the ciphertext while typing in the ciphertext into a similar machine would produce the original plaintext. Since the same sets of wires were used for the forwards and backwards paths across rotors, the reflector also ensured that no letter could be enciphered to itself since that would require the current to flow through the wires in both directions at the same time and this is not possible. This latter feature was designed as an extra security precaution to prevent plaintext from being inadvertently included in the ciphertext message. Unfortunately, rather than improving security, it introduced a weakness into the system which was later exploited by the British codebreakers.
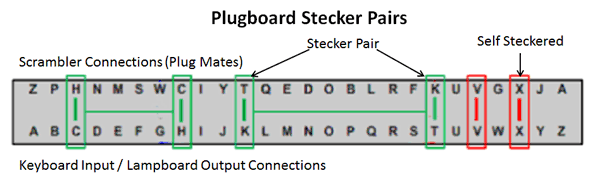
The Enigma machines eventually used by the German Army had two more interchangeable rotors with the facility to select any three from a possible five. This provided a possible 60 permutations of rotor sets and rotor orders multiplying the number of ways of enciphering the text correspondingly. The German Navy extended their rotor library to eight different wheels giving the operator the choice of three from eight or 336 (8 X 7 X 6) possible permutations. The Plugboard - Later versions of Enigma also had a manual plugboard, (commonly called the Stecker-board by British codebreakers after the German Stecker meaning Plug). This was equivalent to a fourth "fixed" rotor, with two sets of 26 sockets with one socket for each letter which enabled further letter substitutions to be made. Since Enigma's reciprocity had to be maintained, it was necessary to connect the letters in reciprocal pairs across the plugboard with pairs of cables. Known as "stecker pairs", examples of these cross connections shown in the diagram below are H "steckered" with C, and T steckered with K. Thirteen such pairs or substitutions are possible but typically only ten cable pairs were used. The remaining six unplugged letters were self-steckered, passing the letters unchanged across the plugboard, (V and X in this example).
The plugboard multiplied the number of possible ways the Enigma could be set up by a further 150,738,274,937,250 times (26!/10!*6!*210).
The principle of reciprocity employed on the plugboard was exploited by Gordon Welchman in his "diagonal board" which shortened the Bombe-runs used by Turing to break Enigma's daily keys. Setting or Key Sheets - The arrangement of Enigma's rotors and the cable links on the plugboard provided a unique series of letter substitutions corresponding to the current path through the machine which changed with each keystroke. The daily rotor order and the ring and plugboard settings to be used were specified in the setting sheets which were distributed each month in a codebook to all users of a network. The Operation - The Enigma operator followed the predetermined plan specified in the settings sheets. First was the selection of the three rotors, from the available bank of five, to be used that day and the planned order in which they were to be placed in the machine. Next was the ring setting to fix the start position offset of each of the three rotors, followed by the setting of the plugboard inter-connections. Because the sender could choose the rotor start settings, it was necessary to inform the recipient of the chosen settings or Grundstellung and this formed the first three letters of the transmitted message. These three letters were actually repeated and sent twice in early transmissions as a "double indicator" to enable the recipient to confirm they had been correctly received. This double indicator was another source of weakness in the system which was exploited by the Polish codebreakers until the Germans eventually abandoned the practice. Once the machine was set up, the operator pushed a plaintext letter on the keyboard and the corresponding ciphertext letter was lit up on the lampboard. (See the "Encipherment Stages" diagram above)
After each keystroke, the Enigma operator noted by hand the ciphertext output symbols appearing on the lampboard and a radio operator subsequently transmitted the complete encrypted message by means of Morse code. At the receiving station, the radio operator received the Morse code and converted into the ciphertext. The Enigma machine operator set up the receiving Enigma machine identically to the transmitting machine and typed in the ciphertext which the machine decrypted into plaintext indicating its output, letter by letter, on the lampboard. Breaking the Enigma CodeIn the early days before World War II, both the Polish and British codebreakers had examples of Scherbius' commercial machines, but not the German military's rotor wheels. The Poles realised that it was necessary to use mathematics to look for patterns to break modern codes and had broken some of the early pre-war German codes while the British were still using linguists for codebreaking. For security reasons there was little exchange of information between the two nations. The imminent outbreak of the war changed all that. The Polish Codebreakers Poland's main codebreakers were Jerzy Rozycki and Henryk Zygalski led by Marian Adam Rejewski who all studied maths at Poznan University and were later recruited into cryptology at Poznan in 1929. Poznan was chosen because many students were German speakers. In 1932 the Poznan department was closed and the staff were moved to the Polish General Staff's Cipher Bureau in Warsaw.
Various methods were devised to simulate the possible permutations of the internal rotor wheel connections, their order and starting positions and to determine their actual configuration from patterns in the ciphertext. The Way In Early systems had a key weakness which was exploited by the Polish codebreakers. The three letters specifying each day's wheel settings were distributed by the operators as the first letters of the message, but because there was a possibility that the message could be garbled, the keys were sent twice. Thus an example setting NKU would be sent twice in succession giving a double indicator in ciphertext of JHN QBG. Thus JHN and QBG would both be ciphertext equivalents of the same message NKU. Zygalski realised that by chance, it is possible that the same letter appears in both the first and second three letter groups of the double indicator keys, depending on the ring settings, thus setting KIE could possibly result in ciphertext of SPE SNT when the message is sent twice in succession. This means that a single letter, in this case K, could possibly be encoded as the same letter, in this case S, when repeated three places later. This occurrence was named at Bletchley as a "female" which was a translation of the word "samiczki" used by the Polish codebreakers. Zygalski's method of determining the rotor starting positions, or ring settings, depended on finding instances "females" that is, letters coded in the same way by different machine cycles. He designed a series of 26 perforated sheets or cards, each with 26 rows representing each of the 26 possible positions on the right (fast) rotor and 26 columns representing the 26 possible positions of the middle rotor. The 676 crossing points between the rows and columns represent the possible connections between the corresponding letters on the right and middle rotors. Knowing the wiring connections of the three rotor wheels, it was possible to determine whether the occurrence of a "female" was possible for all of the starting positions of the right and middle rotors for a given reference position of the left (slow) rotor. At each crossing point, if a "female" was possible, a hole was cut in the card otherwise the card was left blank at that point. The presence of these apertures indicated many possible rotor settings for the right and middle rotors where females might occur for a given reference position of the left rotor. By making 26 similar sheets, one for every starting position of the left rotor, it was possible to narrow the possibility of females down to a single occurrence which represented the starting ring settings for all three rotors. The sheets for the left rotor were superimposed over the reference sheet one by one over a light which shone through the holes in the sheets to indicate the coincidence of "females". As more and more sheets were examined, the number of uncovered apertures was progressively reduced indicating fewer possibilities of "females" until a set of sheets was found which only let light through a single aperture. The starting position programmed into this last sheet indicated the starting position of the left rotor. From this information, and the corresponding crossing point on the reference sheet, a machine could be set up with the correct ring settings to decipher that day's messages. Rejewski was also able to calculate the rotor wiring connections by a different method. Knowing that the first 26 plain text letters all went through the first rotor while the other two rotors remained fixed and did not change the letters, he was able to analyse a whole day's messages to look for patterns in the 26 possible permutations from the first rotor. Together with the clues from the doubly encrypted wheel settings he was able to determining the wiring cross connections in the first rotor. The Polish cryptologists were further helped by the French who had purchased sample coded documents and other information about Enigma from a German traitor named Hans Thilo Schmidt (code name Aché). They learned that the rotor orders were fixed for three months and that the documents covered the period of a changeover giving further clues to the possible patterns in the encryption permutations. From this new information, together with the repeated three letter start settings, Rejewski was able to determine the cross connections in all three of Enigma's rotors and ultimately to design an electro-mechanical machine they called a "Bomba", which emulated the workings of an Enigma's scrambler. Operators could then search for the settings of the Enigma that had encoded the message, by cycling through all the possible rotor settings. Unfortunately the Polish efforts were frustrated just before the war when when the Germans added two more rotors to the Enigma machine increasing the possible wheel orders from 6 to 60 and a plug board dramatically increasing the possible encryption permutations. In May 1940 the Germans also abandoned the doubled indicator keys to the wheel settings on which critical elements of the Polish decryption depended rendering their method useless. The British Codebreakers. On the eve of war in July 1939, five weeks before Germany's invasion of Poland, British codebreakers from Bletchley Park, Alastair Denniston, head of the Government Code and Cipher School (GC&CS), and Dillwyn "Dilly" Knox, GC&CS Chief Cryptographer, together with French cryptanalysts met with members of the Polish Cipher Bureau including Rejewski, Zygalski and Rozycki at a secret facility in a forest in Pyry near Warsaw to share their knowledge. After the meeting, the Poles sent a working clone of the latest German Enigma machine to both the French and the British which they received the following month. Bletchley codebreakers were informed by the Poles about their Bomba and the internal wiring of the three rotors and their reflector in Enigma's scrambler which had been confirmed by subsequent capture of German machines, but the Polish codebreaking methods were no longer valid since the Germans had changed their communications protocols and a new method of deciphering the code had to be found.
Bletchley's cryptanalysts, mathematicians Alan Turing and Gordon Welchman used a "brute force" method modified with ingenious shortcuts to decipher the revised Enigma code. They designed a machine which they called a Bombe which emulated the Enigma scramblers and could cycle through all its possible rotor positions. It did not decrypt the Enigma messages however, instead its purpose was to find the machine's initial settings which provided the key to the decryption. The Bombe was able to determine the order in which the scrambler's rotors had been placed in the machine, the start settings of each rotor and the setting of at least one cable on the plugboard. Once the machine's settings were known, they could be used to set up a similar cipher machine to decipher the original encrypted message and all other messages intercepted the same day. Since every Enigma terminal in the German military network had to communicate with every other terminal in the network, they all had to use the same Enigma settings. This enabled the Bletchley codebreakers to read all German military communications intercepted each day by Allied listening posts. The method depended on guessing a short letter string called a "crib" which may be expected to be part of the plaintext message and using the Bombe to check it against every possible Enigma setting until a plausible match was found in the ciphertext. The machine settings at this point should correspond the settings of the machine which sent the method. Even when carried out by machine, this method could be laboriously long and impractical. The settings were changed every day and as many as 6000 messages per day had to be deciphered. Turing and Welchman devised logical shortcuts to reduced the number of machine cycles needed by the Bombe to find the key to the daily settings. Some were based on weaknesses in the Enigma system design, such as the significance of "crashes" and "reciprocity", overlooked by the Germans. Others such as "loops and menus" were developed by inspired logical reasoning. The ideal crib would be 20 to 30 characters long. Too short would result in too many possibilities to investigate. Too long could result in a turnover when the first rotor caused the second rotor to step forward before the end of the crib string had been read causing the process to be disrupted. German military communications tended to be formal with a stereotypical format. The following are examples of common short text strings often found in German plaintext messages which were used as cribs. Bletchley's Bombe compared the crib with a suitable section of ciphertext and determined which rotors had been used to encipher the text and the corresponding ring settings which had been used as well as one of the plugboard input connections. It did not however provide the full complement of plugboard cross-connections, nor did it decipher the ciphertext message. These remaining tasks were carried out on a Typex machine which replicated all the functions of the basic German Enigma machine with a single 3 rotor scrambler, a keyboard, a plugboard and a lampboard. The Typex machine's rotors were set up to match the Enigma rotor settings indicated by the Bombe's stop position. The operator could then confirm whether the stop was a "true stop" providing a plausible match for the entire ciphertext string or whether it was valid just for the crib, in other words a "false stop". The Typex machine also provided the final key to the Enigma plugboard stecker pairs (see below) which could then be used to set up similar Typex machines to decrypt the day's intercepted communications. As a bonus the machines could be configured to send encrypted messages to other Typex machines. The Bombe's set up with multiple emulators of the Enigma's three rotor scrambler, arranged in a loop, could be used to determine the plugboard cross-connection to the loop's central letter, while the Typex machine was used to determine the rest of the cross-connections. Considering the enormous number of possible plugboard connections (150 X 1012), it turned out to be surprisingly easy. Plug Mates and Stecker Pairs The letter designations of the plugboard's connections to the scrambler were known as the plug-mates of the plugboard's input and output connections. The stecker pairs connected the plugboard inputs and outputs to their plug-mates. In this way, the correct plugboard "steckering" can also be determined from a false plugboard input. Welchman realised that the property of reciprocity as obtained by using stecker pairs in the plugboard could also be used to reduce the number of Bombe cycles needed to evaluate a crib. We know that the scramblers are also reciprocal so that, using the menu above as an example, if X is enciphered to O, O must also be enciphered to X, its stecker partner. Thus, for a particular set of rotor positions, if the input X causes a contradiction, inputting an O would also cause a similar contradiction with the same settings making it unnecessary to make a separate check for the second condition so that the Bombe could move on to the next cycle. This could be implemented by connecting the double ended scrambler's O output back to its O input. More generally, this principle could be applied to all possible scrambler input-output pairs reducing dramatically the number of Bombe cycles necessary to find a stop. The so called diagonal board, named after the appearance of its wiring, enabled this major shortcut and a diagonal board was attached to each scrambler in the Bombe's loops maximising its utility. The diagonal board was a passive circuit board with 26 by 26 electrical terminals connecting all possible inputs of a Bombe's scrambler to all its possible outputs or stecker partners. A 26 way cable, connected between the scrambler's A to Z inputs and the 26 terminals on one side of a square circuit board, while a similar 26 way cable was connected between the scrambler's output terminals and the 26 terninals on the adjacent side of the diagonal board. The the 26 rows and columns of the board's wiring were permanently cross connected in pairs corresponding to the symmetrical property of the steckers, so that for example the terminal in row X, column O is connected to the terminal in row O, column X, a total of 325 pairings. In operation, no switching was required and only one pair of wires connected through the board was live when the crib matched the ciphertext and this pair corresponded to the current position of the scrambler's rotors. In summary, the use of the simple inexpensive diagonal boards greatly increased the number of contradictions derived from any false initial hypothesis occurring in each Bombe cycle so that it needed far fewer cycles to find rotor settings matching the crib to the ciphertext resulting in much shorter Bombe runs and in addition, the matching also became possible with shorter cribs. The Legacy Historians generally agree that breaking the German codes shortened the war by two years and consequently saved countless lives. Apart from breaking the code, another major achievement of the British codebreakers was that the Germans never realised that their system had been compromised. It depended on maintaining a discipline of absolute secrecy of the thousands of people employed at Bletchley Park and remote government listening stations (Y stations) and also control of how the information gleaned from the messages was used and supported by subterfuge, deception and misinformation so as not to alert the Germans that the British and their Allies might have information they were not expected to have. The company which designed the Bombe, BTM, after several mergers and takeovers is now ironically part of a Japanese/German joint venture between Fujitsu - Siemens.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
![]() Print This Page || Home || FAQ || Site Map || Legal || Privacy Promise || Contacts
Print This Page || Home || FAQ || Site Map || Legal || Privacy Promise || Contacts
Woodbank Communications Ltd, South Crescent Road, Chester, CH4 7AU, (United Kingdom)
Copyright © Woodbank Communications Ltd 2005